This is a four part blog post series that starts with Rustproofing Linux (Part 1/4 Leaking Addresses). This post uses a simple example to demonstrate a class of vulnerability that we encounter quite frequently when auditing kernel drivers and firmware. It’s a race condition, or more precisely a TOCTOU vulnerability. The complete vulnerable C driver … Continue reading Rustproofing Linux (Part 2/4 Race Conditions) →
...moreSummary
Total Articles Found: 18
Top sources:
Top Keywords:
- Research: 11
- Tool Release: 5
- Cloud & Containerization: 4
- Hardware & Embedded Systems: 3
- Pentesting: 3
Top Authors
- Jeff Dileo: 4
- Domen Puncer Kugler: 1
- Jose Selvi: 1
- Jennifer Fernick: 1
- Catalin Visinescu: 1
Top Articles:
- Tool Release – Enumerating Docker Registries with go-pillage-registries
- An offensive guide to the Authorization Code grant
- A Survey of Istio's Network Security Features
- Deep Dive into Real-World Kubernetes Threats
- ScoutSuite 5.8.0 Released
- ABSTRACT SHIMMER (CVE-2020-15257): Host Networking is root-Equivalent, Again
- Public Report – Pixel 4/4XL and Pixel 4a ioXt Audit
- LDAPFragger: Bypassing network restrictions using LDAP attributes
- Bypassing software update package encryption – extracting the Lexmark MC3224i printer firmware (part 1)
- Tool Release: Sinking U-Boots with Depthcharge
Rustproofing Linux (Part 2/4 Race Conditions)
Published: 2023-02-08 15:41:37
Popularity: None
Author: Domen Puncer Kugler
Keywords:
Using Semgrep with Jupyter Notebook files

Published: 2023-01-26 01:01:00
Popularity: None
Author: Jose Selvi
Keywords:
If you frequently deliver source code review assessments of products, including machine learning components, I’m sure you are used to reviewing Jupyter Notebook files (usually python). Although I spend most of my time reviewing the source code manually, I also use static analysis tools such as semgrep, using both public and private rules. This tool … Continue reading Using Semgrep with Jupyter Notebook files →
...moreTechnical Advisory – BLE Proximity Authentication Vulnerable to Relay Attacks

Published: 2022-05-16 17:38:30
Popularity: None
Author: Jennifer Fernick
🤖: ""relay attack fail""
NCC Group has developed a tool for conducting a new type of BLE relay attack operating at the link layer, for which added latency is within the range of normal GATT response timing variation, and which is capable of relaying encrypted link layer communications. This approach can circumvent the existing relay attack mitigations of latency bounding or link layer encryption, and bypass localization defences commonly used against relay attacks that use signal amplification.
...moreBypassing software update package encryption – extracting the Lexmark MC3224i printer firmware (part 1)

Published: 2022-02-17 10:25:41
Popularity: 1
Author: Catalin Visinescu
Keywords:
Lexmark encrypts the firmware update packages provided to consumers, making the binary analysis more difficult. With little over a month of research time assigned and few targets to look at, NCC Group decided to remove the flash memory and extract the firmware using a programmer, firmware which we (correctly) assumed would be stored unencrypted. This allowed us to bypass the firmware update package encryption. With the firmware extracted, the binaries could be reverse-engineered to find vulnerabilities that would allow remote code execution.
...moreTool Release – insject: A Linux Namespace Injector

Published: 2022-01-08 05:20:06
Popularity: None
Author: Jeff Dileo
Keywords:
🤖: "Linux namespace party"
tl;dr Grab the release binary from our repo and have fun. Also, happy new year; 2021 couldn’t end soon enough. Background A while back, I was asked by one of my coworkers on the PSC team about ways in which to make their custom credit card data scanner cloud native to assess Kubernetes clusters. While … Continue reading Tool Release – insject: A Linux Namespace Injector →
...moreTool Release – shouganaiyo-loader: A Tool to Force JVM Attaches
🤖: "Java crashes again"
Background Java Virtual Machines (JVMs) provide a number of mechanisms to inspect and modify the Java applications and the runtime they stand on. These include Java agents, JARs that are capable of modifying Java class files at runtime; and JVMTI agents, native libraries that can perform deep hooking into the innards of the JVM itself. … Continue reading Tool Release – shouganaiyo-loader: A Tool to Force JVM Attaches →
...moreTechnical Advisory – New York State Excelsior Pass Vaccine Passport Scanner App Sends Data to a Third Party not Specified in Privacy Policy

Published: 2021-09-01 19:00:00
Popularity: None
Author: Dan Hastings
Keywords:
🤖: ""Data breach alert""
Summary The New York State (NYS) Excelsior scanner app is used by businesses or event venues to scan the QR codes contained in the NYS Excelsior wallet app to verify that an individual has either a negative COVID-19 test or their vaccination status. We have found that some data about the businesses/event venues using the app … Continue reading Technical Advisory – New York State Excelsior Pass Vaccine Passport Scanner App Sends Data to a Third Party not Specified in Privacy Policy →
...moreSome Musings on Common (eBPF) Linux Tracing Bugs

Published: 2021-08-06 04:54:28
Popularity: None
Author: Jeff Dileo
Keywords:
Having been in the game of auditing kprobe-based tracers for the past couple of years, and in light of this upcoming DEF CON on eBPF tracer race conditions (which you should go watch) being given by a friend of mine from the NYU(-Poly) (OSIR)IS(IS) lab, I figured I would wax poetic on some of the … Continue reading Some Musings on Common (eBPF) Linux Tracing Bugs →
...moreABSTRACT SHIMMER (CVE-2020-15257): Host Networking is root-Equivalent, Again

Published: 2020-12-10 15:00:00
Popularity: 4
Author: Jeff Dileo
Keywords:
This post is a technical discussion of the underlying vulnerability of CVE-2020-15257, and how it can be exploited. Our technical advisory on this issue is available here, but this post goes much further into the process that led to finding the issue, the practicalities of exploiting the vulnerability itself, various complications around fixing the issue, … Continue reading ABSTRACT SHIMMER (CVE-2020-15257): Host Networking is root-Equivalent, Again →
...morePublic Report – Pixel 4/4XL and Pixel 4a ioXt Audit

Published: 2020-08-10 13:00:00
Popularity: 4
Author: Jameson Hyde
Keywords:
NCC Group was contracted by Google to conduct a security assessment of the Pixel 4, Pixel 4XL, and Pixel 4a devices. This assessment was specifically focused on determining whether the devices comply with the ioXt Android Profile based on the ioXt Security Pledge. This assessment was performed between July 28 and August 7, 2020. The Google … Continue reading Public Report – Pixel 4/4XL and Pixel 4a ioXt Audit →
...moreTool Release: Sinking U-Boots with Depthcharge

Published: 2020-07-22 16:00:49
Popularity: 1
Author: Jon Szymaniak
Keywords:
Depthcharge is an extensible Python 3 toolkit designed to aid security researchers when analyzing a customized, product-specific build of the U-Boot bootloader. This blog post details the motivations for Depthcharge’s creation, highlights some key features, and exemplifies its use in a “tethered jailbreak” of a smart speaker that leverages secure boot functionality. I boot, you … Continue reading Tool Release: Sinking U-Boots with Depthcharge →
...moreAn offensive guide to the Authorization Code grant

Published: 2020-07-07 11:00:01
Popularity: 17
Author: Rami McCarthy
Keywords:
OAuth is the widely used standard for access delegation, enabling many of the “Sign in with X” buttons and “Connect your Calendar” features of modern Internet software. OAuth 2.0 is the most common and recent version of this specification, which defines four grant types (as well as various extensions), specifically suited for different use cases. … Continue reading An offensive guide to the Authorization Code grant →
...moreScoutSuite 5.8.0 Released
🤖: "Cyber tools ahead"
Quick note to say we’ve released ScoutSuite 5.8.0 on Github: Improved support for AWS Added support for KMS Added basic support for Secrets Manager Simplified evaluation of IAM policies in multiple rules Improved support for Azure Added support for App Service Web Apps Added support for Security Center Compliance Results Added support for Security Center … Continue reading ScoutSuite 5.8.0 Released →
...moreLDAPFragger: Bypassing network restrictions using LDAP attributes
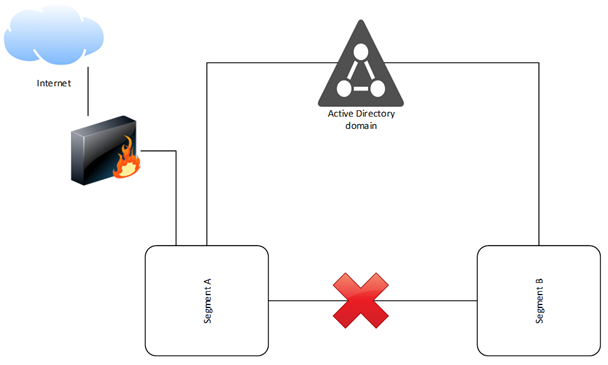
Published: 2020-03-19 10:00:00
Popularity: 4
Author: Rindert Kramer
Keywords:
Introduction A while back during a penetration test of an internal network, we encountered physically segmented networks. These networks contained workstations joined to the same Active Directory domain, however only one network segment could connect to the internet. To control workstations in both segments remotely with Cobalt Strike, we built a tool that uses the … Continue reading LDAPFragger: Bypassing network restrictions using LDAP attributes →
...moreA Survey of Istio's Network Security Features

Published: 2020-03-04 12:00:00
Popularity: 12
Author: jleadfordncc
Keywords:
🤖: "Secure network gates"
Istio is a service mesh, which, in general, exist as a compliment to container orchestrators (e.g. Kubernetes) in order to provide additional, service-centric features surrounding traffic management, security, and observability. Istio is arguably the most popular service mesh (using GitHub stars as a metric). This blog post assumes working familiarity with Kubernetes and microservices, but … Continue reading A Survey of Istio's Network Security Features →
...moreDeep Dive into Real-World Kubernetes Threats

Published: 2020-02-12 12:00:00
Popularity: 8
Author: nccmanning
Keywords:
On Saturday, February 1st, I gave my talk titled “Command and KubeCTL: Real-World Kubernetes Security for Pentesters” at Shmoocon 2020. I’m following up with this post that goes into more details than I could cover in 50 minutes. This will re-iterate the points I attempted to make, walk through the demo, and provide resources for … Continue reading Deep Dive into Real-World Kubernetes Threats →
...moreProperly Signed Certificates on CPE Devices

Published: 2020-02-04 09:04:08
Popularity: None
Author: m4ttlewis
Keywords:
🤖: ""Secure Certs Only""
During late January 2020, a hot topic surfaced between security professionals on an issue that has historically had different proposed solutions. This blog post seeks to explore these solutions and identify pragmatic approaches to risk reduction on this specific issue concerning Customer Premises Equipment (CPE) security. Two security researchers (Tom Pohl and Nick Starke) analysed … Continue reading Properly Signed Certificates on CPE Devices →
...moreTool Release – Enumerating Docker Registries with go-pillage-registries

Published: 2020-01-24 13:15:00
Popularity: 42
Author: jmakinenncc
Keywords:
🤖: "docker hack!"
Introduction Containerization solutions are becoming increasingly common throughout the industry due to their vast applications in logically separating and packaging processes to run consistently across environments. Docker represents these processes as images by packaging a base filesystem and initialization instructions for the runtime environment. Developers can use common base images and instruct Docker to execute … Continue reading Tool Release – Enumerating Docker Registries with go-pillage-registries →
...more
